Cybersecurity risks faced by central banks
August 18, 2023
Cybersecurity risks faced by central banks
Cybercrimes have increased frequently over the past several years to the point where it is thought that they are one of the most significant hazards to the financial sector. The consequences of a successful cyberattack on a central bank can be severe. They can include financial losses, damage to reputation, and disruption to financial markets. Central banks are taking steps to mitigate these risks, but the threat of cyberattacks is constantly evolving. The most common cyber security risks faced by Central banks entail:
-
Phishing and social engineering: These are the most common methods of attack, and they can be used to trick employees into revealing sensitive information or clicking on malicious links. They can be used to enter a financial institution's network and conduct a more severe attack like APT.
-
Advanced persistent threats (APTs): These are targeted attacks that are often launched by state-sponsored actors. They can be very sophisticated and difficult to detect.
-
Trojans: It is a malicious computer application created to access private data processed or kept by online banking systems. This kind of computer program has a backdoor that enables access to a computer from the outside. According to IMF, there are roughly 54,000 [1] installation packages for mobile banking trojans in 1st quarter of 2022.
-
Ransomware: This type of attack encrypts a victim's data and demands a ransom payment in exchange for the decryption key. Almost 90% [2] of banking institutions have faced ransomware in the past year hence it poses a severe threat to them.
-
Distributed denial-of-service (DDoS) attacks: These attacks send a flood of traffic to the target server or network, overwhelming it and preventing it from responding to legitimate requests. This can cause the target to become unavailable to users, or to slow down significantly. They may include different methods like volumetric, protocol, or application-layer attacks to disrupt the system.
-
Supply chain attacks: These attacks target the suppliers of central banks, such as cloud providers or software vendors. If a supplier is compromised, the attackers can gain access to the central bank's systems.
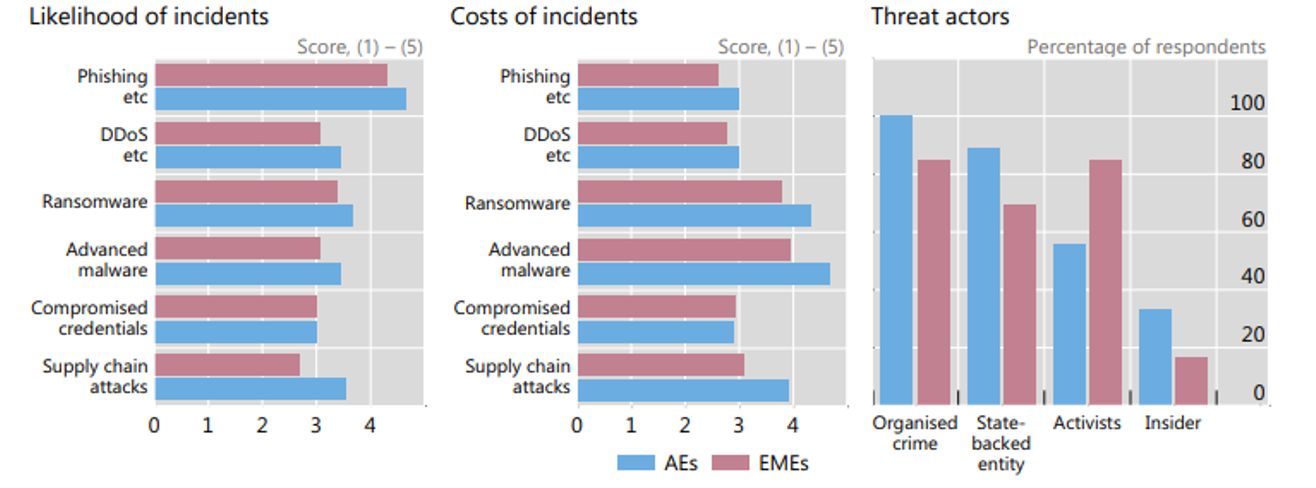
Cyber security risks faced by the Bank assume paramount importance from the mere fact that the Reserve Bank of India (RBI) reported bank frauds of around ₹61 thousand crores in 2022 [3]. The figure below shows the various cybersecurity incidents observed in advanced economies and emerging market economies on a score scale of 0 (least likely) to 5 (highly likely).
International Best practices
International Banking organizations like International Monetary Fund, European Central Bank, Bank of International Supervision regularly release guidelines and reports on cybersecurity to ensure a strong collaboration amongst the member banks. The guidelines provide a framework for central banks worldwide to become resilient and robust against cybersecurity risks. These also assist in the assessment of risk and prioritizing the areas of expertise that Banks must pursue to strengthen their IT infrastructure for protection against attacks. The following are some of the best practices that are recommended:
-
Using zero trust in combination with a VPN:
- Virtual private networks provide a safe gateway to connect to systems over the internet, but they might present scalability challenges. VPN technology may be prone to cyber-attacks and vulnerabilities like Man-in-the-middle attacks and DNS Spoofing and SSL stripping. In contrast, the zero-trust approach inherently assumes every connection as untrustworthy and verifies all procedures at the client's end. Zero-trust follows a stateless architecture that allows the solution to be secure and scalable.[4]
-
Artificial Intelligence & Machine Learning:
-
Fraud detection: AI and ML can be used to identify fraudulent transactions by analyzing patterns in data. This can help banks to prevent fraud and protect sensitive information
-
Malware detection: detect malware by analyzing its behavior. This can help banks to prevent malware from infecting their systems and stealing their data.
-
Risk assessment: assess the risk of a cyberattack by analyzing a bank's environment. This can help banks to prioritize their security efforts and make informed decisions about how to protect themselves.
-
Security automation: automate security tasks, such as vulnerability scanning and patch management. This can help banks to save time and resources and to improve the efficiency of their security operations.
-
-
Developing cloud security:
- The rapid rise of cloud migration has left little time for stringent cybersecurity measures. Secured networks and on-premises cloud services often provide the highest standards of security and safety.[4]
-
Monitor the activity of privileged and third-party users:
-
User activity monitoring (UAM) can help you increase visibility, detect malicious activity, and collect evidence for forensic investigations. UAM solutions collect a variety of data about user activity, including web browsing activity, application usage, network activity, and keystroke logging. By collecting this data, UAM solutions can provide organizations with a detailed overview of user activity. This information can be used to identify suspicious activity, such as:
- Unauthorized access to sensitive data: This could include attempts to access files, applications, or networks that a user should not have access to.
- Data exfiltration: This could include attempts to copy sensitive data to an external device, such as a USB drive or cloud storage account.
- Malware infection: This could include attempts to install malware on a user's device.
-
-
Stricter requirements for cybersecurity compliance:
-
Implementation of strong security controls encompassing strong passwords, multi-factor authentication, and encryption. Encryption acts as the strongest link and industry standard EC25519 provides the highest standard of security. [5] Additional security controls can be implemented to further protect sensitive data, they may include:
- Access control: This involves restricting access to sensitive data to authorized users only. This can be done by implementing role-based access control (RBAC), which assigns different levels of access to different users based on their job roles.
- Data loss prevention (DLP): This technology helps to prevent sensitive data from being leaked or lost. DLP solutions can monitor data flows and identify and block unauthorized attempts to transfer sensitive data.
- Vulnerability scanning: This involves regularly scanning systems for vulnerabilities that could be exploited by attackers. Vulnerability scanners can identify security flaws in software, operating systems, and network devices.
-
-
Breach and attack simulation platform:
- A breach and attack simulation platform is a software tool that tests the vulnerability of an organization's IT infrastructure by simulating real-world cyberattacks. The platform provides feedback and analysis to help organizations identify and mitigate blind spots in their cybersecurity. The platform typically works by using a variety of techniques to mimic the tactics, techniques, and procedures (TTPs) used by actual cyber criminals. These techniques can include:
-
Sending phishing emails
-
Exploiting known vulnerabilities
-
Gaining unauthorized access to systems
-
Moving laterally through a network
-
Exfiltrating data
-
-
The platform then tracks the progress of the simulated attack and provides feedback to the organization on how it could have been prevented. This feedback can include:
- A list of vulnerabilities that were exploited
- The steps that the attacker took to gain access
- Recommendations for how to mitigate the vulnerabilities
- A breach and attack simulation platform is a software tool that tests the vulnerability of an organization's IT infrastructure by simulating real-world cyberattacks. The platform provides feedback and analysis to help organizations identify and mitigate blind spots in their cybersecurity. The platform typically works by using a variety of techniques to mimic the tactics, techniques, and procedures (TTPs) used by actual cyber criminals. These techniques can include:
-
Augmenting supply chain infrastructure to help businesses to improve their efficiency, reduce their costs, improve customer service, and increase their agility[6].
- Employing multiple vendors and n+1 redundancy to avoid a single point of failure.
- Cloud computing can be used to store and process data, and to provide access to applications and services. Creating redundancy and safety across geo-locations.
- IoT devices can be used to collect data about the physical environment. This data can be used to improve warehouse efficiency, optimize transportation, and prevent fraud.
-
User awareness:
- The customer must be made aware of the fact that they must not disclose their credentials to anybody. The user is the weakest link and must be informed about the various cyber risk activities like social engineering, phishing, snooping, password hacking, etc. Awareness activities like awareness events, posters, seminars and team discussions play an important role in preventing attacks. The Bank must provide Specific Training for High Risk or Sensitive Groups and the programmes should be provided at least annually to all staff.
-
Penetration Testing:
- Penetration testing serves as a proactive measure to try to identify vulnerabilities in services and organizations before other attackers can[6]. Pen-Testing can help banks and financial institutions in the following ways:
-
Identify vulnerabilities. It can help identify vulnerabilities in an organization's IT infrastructure and applications that could be exploited by cybercriminals. By finding these vulnerabilities, the organization can take steps to remediate them before they are exploited.
-
Meet regulatory compliance requirements. Many regulatory bodies, banks and financial institutions perform regular penetration testing. This helps to ensure that these organizations are taking appropriate steps to protect sensitive data.
-
Test security controls. Penetration testing can help test the effectiveness of security controls, such as firewalls, intrusion detection systems, and other security measures that are in place. It helps to determine if these controls are functioning as intended and if they are providing adequate protection against potential threats.
-
Keep up with emerging threats. Cyber threats are constantly evolving, and organizations need to stay on top of these threats to protect their systems and data. Penetration testing can help organizations identify and mitigate new threats as they emerge.
-
- Exercises like red teaming and purple teaming fall under the purview of technical Pen-Testing.
- Penetration testing serves as a proactive measure to try to identify vulnerabilities in services and organizations before other attackers can[6]. Pen-Testing can help banks and financial institutions in the following ways:
-
Control access to sensitive data:
- Using the principle of least privilege to assign each user the fewest access rights possible and elevating privileges only if necessary. If access to sensitive data is not needed, corresponding privileges should be revoked. In addition to the principle of least privilege and the zero-trust model, a just-in-time approach to access management brings even more granularity to controlling user privileges. This approach means providing employees access by request for a specific time and a valid reason.
-
Formulation of an incident response[7]:
- In case of a successful cyber-attack, the financial institutions must have internal policies and SOPs in place to respond appropriately to the attack. The response plan may follow:
- The internal processes for responding to a cybersecurity event
- The goals of the incident response plan
- The definition of clear roles, responsibilities, and levels of decision-making authority
- External and internal communications and information sharing
- Identification of requirements for the remediation of any identified weaknesses in Information Systems and associated controls
- Documentation and reporting regarding Cybersecurity Events and related incident response activities
- In case of a successful cyber-attack, the financial institutions must have internal policies and SOPs in place to respond appropriately to the attack. The response plan may follow:
-
Technological collaboration:
-
Technological companies are at the forefront of cyber-attacks and provide updates and patches against day-zero attacks. The Bank and technological companies must work to explore the blind spots in the implementation and application of technology. Partnerships with international organizations will foster an ecosystem that will result in increased collaboration. The various aspects of collaboration may include:
- Threat intelligence
- Training/staff exchanges
- Project support
- Building capacity
- Maturity of security domains
-
-
Internal Audit Body[7]:
-
Banks should incorporate qualified information and communication technology (ICT) auditors within their Internal Audit team. ICT audit function can be outsourced or through internal placement. The PSP's internal ICT auditors should therefore ensure that the audit scope includes and is not limited to the tasks below:
- Continuous review and report on cyber risks and controls of the ICT systems within the Banks and other related third-party connections.
- Conduct up-front due diligence to mitigate risks associated with third parties. Assess both the design and effectiveness of the cybersecurity framework implemented.
- Conduct regular independent threat and vulnerability assessment tests.
- Report to the board the findings of the assessments.
- Conduct comprehensive penetration tests.
-
-
Strategic Planning and operations:
- Central banks should increase their cyber resilience through enhanced processes and stringent operational checks. A few initiatives recommended are:
- Strengthen the cyber resilience and security posture
- Build and launch the Security Operations Centre (SOC) capabilities and perform periodic evaluation exercises.
- Enhance cybersecurity risk management and security assurance activities during the evaluation, development or acquisition of new and existing information technology projects and systems.
- Adopt a cloud computing strategy.
- Central banks should increase their cyber resilience through enhanced processes and stringent operational checks. A few initiatives recommended are:
-
Provide regulation and guidance to the banking sector:
- Sets out the Central Bank's expectations concerning cybersecurity.
- Strikes a balance between principles and prescription.
- Provides effective guidance to institutions that are at different levels of sophistication.
- Covers key areas such as governance, risk management, IT resilience, and Third-Party risks.
- Can be used as a guide for other financial sector participants to adopt.
International Cybersecurity Frameworks for Banks
A cybersecurity framework provides a common language and set of standards for security leaders across countries and industries to understand their security postures and those of their vendors. With a framework, it becomes easier to define the processes and procedures your organization must take to assess, monitor, and mitigate cybersecurity risk. Some of the common financial cybersecurity frameworks:
-
NIST Cybersecurity Framework[8]
The NIST (National Institute of Standards and Technology) Cybersecurity Framework was created for increased cooperation between the public and private sectors for recognizing, analyzing, and managing cyber risk. NIST has emerged as the gold standard for evaluating cybersecurity maturity, detecting security weaknesses, and adhering to cybersecurity legislation even when compliance is optional.
-
The Bank of England's CBEST Vulnerability Testing Framework
CBEST vulnerability testing methodology was developed by the UK Financial Authorities in collaboration with CREST (the Council for Registered Ethical Security Testers) and Digital Shadows. It is an intelligence-led testing framework. CBEST leverages intelligence from reputable commercial and government sources to find possible attackers for a specific financial institution. Then, it imitates these potential attackers' methods to see how successfully they can breach the institution's Defences. This enables a company to identify the weak points in its system and create and implement corrective action plans.
-
Cybersecurity and Privacy Framework for Privately Held Information Systems (the CIPHER Framework)
Computer systems that organizations, both public and private, control and that hold personal data gathered from their clients are referred to as PHISs (Privately Held Information Systems). CIPHER framework addresses electronic systems, digital information kinds, and methods for data sharing, processing, and upkeep (not paper documents). The CIPHER methodological framework's primary goal is to suggest procedures and best practices for protecting privately held information systems online (PHIS). The following are the main features of CIPHER methodological framework:
- Technology independence (versatility) refers to the ability to be used by any organization functioning in any field, even as existing technologies deteriorate or are replaced by newer ones.
- PHIS owners, developers, and citizens are the three primary users who focus on this user-centric approach.
- Practicality - outlines possible precautions and controls to improve or verify whether the organization is safeguarding data from online dangers.
- It is simple to use and doesn't require specialized knowledge from businesses or individuals.
Cybersecurity compliance by Bank of International Settlements (BIS)
The Bank for International Settlements (BIS) is an international organization that seeks to promote financial stability and cooperation among central banks. The BIS has published several reports and papers on cybersecurity compliance that provide guidance on how central banks can assess their cybersecurity risks and implement effective cybersecurity measures.
- Cybersecurity and Financial System Resilience Report (2022)
- Cybersecurity for Central Banks: A Framework for Assessment and Enhanced Resilience (2016)
- Cyber Resilience in Central Banks: Managing Risks from Systemic Disruptions (2017)
- Cybersecurity in Central Banking: Building Effective Governance, Risk Management, and Culture (2018)
These frameworks are based on the principles of Risk-based assessment, comprehensive 360° security and continuous improvement.
Cybersecurity resilience guidelines by European Central Bank
ECB works in tandem with various stakeholders to facilitate a comprehensive framework that is resilient and robust against cyber-attacks. The main areas of focus are:
- Cooperation with Banks and neighboring Central Banks
- Cooperation with other National institutions
- Cooperate with National Cyber Security Authorities
- Encourage information exchange
- Promote cyber resilience among financial market infrastructures
- Monitor and supervise Bank's IT risk
- Participate in meetings and working groups
Future Outlook
The Internet and related ICTs are becoming increasingly central to the economic prosperity of developing and developed nations. However, the benefits of the Internet and related technologies are contingent on maintaining a level of security, trust, and openness of a global Internet. The COVID-19 pandemic has exacerbated possible fintech and cybersecurity risks for central banks even further.
Two IMF COVID-19 Special Series Notes highlight specific risk management issues that central banks (could) face in trying to deal with the pandemic and its consequences; another Note highlights the general cybersecurity risks related to working-from-home arrangements.
There is no solution to cybersecurity—no Deus Ex Machina on the horizon. It is a constantly moving target that will entail a continually evolving set of processes to contain the security risks associated with the use of the Internet.
[1] "Cybersecurity In Banking: Importance, Threats, Challenges," [Online]. Available: https://www.cloudibn.com/blogs/importance-of-cybersecurity-in-banking-threats-challenges/.
[2] "Cyber Security Statistics," [Online]. Available: https://purplesec.us/resources/cyber-security-statistics/.
[3] RBI, "RBI Report on Trends and Progress of Banking in India, 2021-22," RBI, 2022.
[4] L. G. Sebastian Doerr, "BIS Working Papers Cyber risk in central banking," BIS, 2022.
[5] "Cybersecurity Risks and Central Banks' Sentiment on Central Bank Digital Currency: Evidence from Global Cyberattacks".
[6] "Elliptic Curve Cryptography (ECC) Central Bank Implementation," [Online]. Available: https://cryptobook.nakov.com/asymmetric-key-ciphers/elliptic-curve-cryptography-ecc.
[7] B. O. G. O. T. F. R. SYSTEM, "Cybersecurity and Financial System," 2022.
[8] C. B. o. T. a. Tobago, "Cybersecurity in Financial Institutions: Best Practices," 2023.
[9] NSIT, "Framework for Improving Critical Infrastructure Cybersecurity," 2014. [Online]. Available: https://www.nist.gov/system/files/documents/cyberframework/cybersecurity-framework-021214.pdf.
